Securing Your **IoT Device AWS IoT SSH** Connections: A Modern Guide
Connecting to and managing distant physical objects has become a big part of how we do things, wouldn't you say? These objects, often called "things," are everywhere now, from smart home gadgets to industrial sensors. Keeping these devices working right and, very importantly, keeping them safe from unwanted access is a big deal. This is especially true when you need to get in there and fix something or check on a device that's far away.
Many folks wonder how to safely talk to these tiny computers once they are out in the world. Getting direct access to them, much like you would a regular computer, is sometimes needed for troubleshooting or updates. This is where the idea of using something like SSH, a way to securely get into a device from afar, comes into play, particularly when those devices are hooked up to a big cloud service like AWS IoT. So, how do we make sure this connection is sound and protected?
This article will help you sort out how to manage your **IoT device AWS IoT SSH** setup safely. We will look at why remote access is helpful, what AWS IoT offers, and how to use SSH in a way that keeps your devices and your information secure. It’s about making sure your connected items stay dependable and private, and that, you know, is pretty important.
Table of Contents
- What Exactly is IoT?
- Why Remote Access Matters for IoT
- AWS IoT: Your Cloud Partner for Devices
- The Role of SSH in Device Management
- Why IoT Device AWS IoT SSH Needs Special Care
- Making IoT Device AWS IoT SSH Secure on AWS
- Practical Steps for Secure IoT Device AWS IoT SSH Setup
- Common Questions About IoT Device AWS IoT SSH
- Keeping Your IoT Device AWS IoT SSH Setup Safe and Sound
- Conclusion
What Exactly is IoT?
The Internet of Things, or IoT, is a pretty interesting idea. According to many experts, it's about connecting various physical items, like sensors and devices, to a network. This allows them to gather and send data without needing a person to step in directly. It's more or less about making everyday objects smart and connected.
These items can be anything from your home appliances to parts of a car, and they come with special bits of computer code and sensors. The main goal, you know, is to let them talk to each other and to cloud services. This way, we can keep an eye on things or control them from a distance, which is actually quite handy.
The whole point of IoT is to let the physical world become digitally watched or managed. It's a vast collection of objects with tiny computers inside that can share information. The term was first thought up by computer scientists, and it describes a network of these "things" that swap data with other IoT devices and the cloud.
Why Remote Access Matters for IoT
Imagine having a bunch of sensors scattered across a large farm or in different parts of a factory. Getting to each one physically every time you need to check something or make a change would be incredibly time-consuming, and honestly, a bit impractical. This is where reaching devices from afar really helps out.
Remote access lets you look at what your devices are doing, fix problems, or put new software on them without actually being there. This is a big plus for devices in hard-to-reach spots or those deployed in very large numbers. It makes managing your connected items much simpler, so.
Being able to get into your devices remotely also means you can respond quickly if something goes wrong. If a sensor stops sending data, you can often log in and see what's happening right away, possibly restarting it or adjusting its settings. This quick action can save a lot of trouble, and it just makes things smoother.
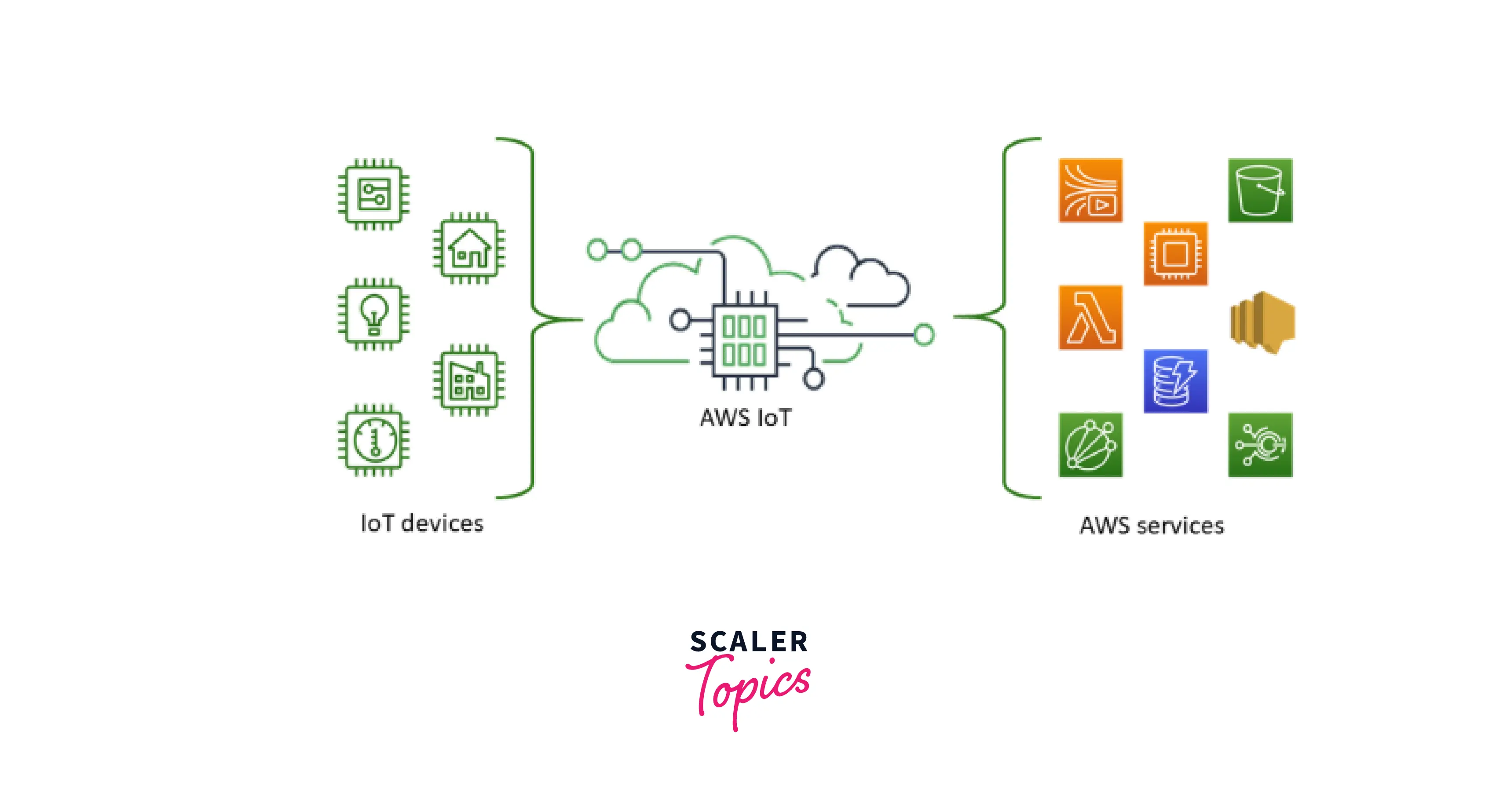
AWS IoT: Your Cloud Partner for Devices
AWS IoT is a service from Amazon Web Services that helps you connect your IoT devices to the cloud. It's like a central hub where all your devices can send their data and receive commands. This service is built to handle a very, very large number of devices, which is pretty useful for big projects.
It offers a lot of tools to manage your devices, from making sure they are who they say they are, to processing the data they send. AWS IoT also provides ways to secure these connections, which is a major concern for anyone working with connected items. It's designed to be a pretty complete solution for device connectivity.
With AWS IoT, you can also set up rules that decide what happens to the data your devices send. For instance, you could have a rule that stores temperature readings in a database or triggers an alert if a certain temperature is reached. This makes it a powerful platform for building smart systems, you know.
The Role of SSH in Device Management
SSH, which stands for Secure Shell, is a way to get into a computer or device over an unsecured network, but in a very safe way. It provides a secure channel for sending commands and getting information back. For many years, it's been a go-to tool for system administrators to manage servers remotely.
For IoT devices, SSH can be just as useful. It allows developers and support teams to connect directly to a device's operating system. This is handy for running diagnostic tests, installing software updates, or changing settings that aren't available through other cloud services. It's a direct line to the device itself.
However, using SSH with IoT devices brings its own set of things to think about. While SSH itself is secure, how you set it up and manage the access can create weak spots. This is especially true given that IoT devices might be less protected than a typical server, or they might be out in the open, so to be honest.
Why IoT Device AWS IoT SSH Needs Special Care
Using SSH with your connected devices, especially when they are tied to a cloud service like AWS IoT, needs a good amount of thought. It's not just about turning it on; it's about making sure it's done right to prevent problems. There are a few reasons why this particular combination needs extra attention.
For one thing, IoT devices are often deployed in places where they might be physically accessible to unauthorized people. If someone gets their hands on a device, and its SSH access isn't locked down, that could be a serious issue. So, keeping that access tight is pretty important.
Also, a lot of IoT devices have limited computing power and memory. This means they might not be able to handle all the fancy security measures that bigger computers can. This makes finding the right balance between usefulness and protection a bit of a challenge, as a matter of fact.
Traditional SSH Risks
Even in a regular computer setup, SSH has some common risks if not handled well. For example, using simple passwords is a big no-no. If someone guesses a password, they can get full control of your device. That's why strong, complex passwords or, better yet, key-based logins are always suggested.
Another risk is leaving SSH open to the whole internet. If your device's SSH port is exposed, bad actors can constantly try to break in. This is called a brute-force attack, and it can eventually succeed if you don't have good protections in place. So, limiting who can even try to connect is a good move.
Also, keeping your SSH software up to date is quite important. Older versions might have known weaknesses that attackers could use. Regularly checking for and applying updates helps close these potential gaps. It's just good practice for any system, really.
IoT Specific Vulnerabilities
IoT devices face some unique problems when it comes to security. Many of them are designed to be cheap and small, which sometimes means security features get left out or are not as strong. This can make them easier targets for people looking to do harm.
Another point is that IoT devices often have a very long lifespan. They might be in use for many years, sometimes even decades. Over such a long time, new security problems can show up, and it might be hard to update older devices. This makes ongoing protection a bit tricky, you know.
Furthermore, many IoT devices are part of a larger system. If one device gets compromised, it could potentially be used as a way to get into other devices or even the main network. This kind of chain reaction is a big concern, so protecting each link is vital, as a matter of fact.
Making IoT Device AWS IoT SSH Secure on AWS
AWS offers several ways to make your **IoT device AWS IoT SSH** connections much safer. Instead of just opening up an SSH port to the internet, which is generally a bad idea for IoT devices, you can use AWS services to create a secure path. This helps keep things locked down while still allowing access when needed.
The goal is to make sure that only authorized people can connect to your devices, and that the connection itself is encrypted. This means that even if someone were to somehow intercept the data, they wouldn't be able to read it. It's about building layers of safety, you know.
Using the right AWS tools can help you avoid many of the common SSH risks we talked about earlier. These tools are designed to work well together and provide a strong security stance for your connected items. It's about being proactive rather than reactive, really.
Leveraging AWS IoT Device Shadow and Jobs
AWS IoT Device Shadow is like a digital twin of your device in the cloud. It keeps track of the device's last reported state and its desired state. You can use this shadow to send commands to your device indirectly, without needing a direct SSH connection.
For example, you could update the device shadow to tell a device to enable SSH for a short time. Then, the device would see this change and open SSH. Once the task is done, you could update the shadow again to tell the device to close SSH. This is a very controlled way to manage access.
AWS IoT Jobs lets you send commands or software updates to a group of devices. You could create a job to push an SSH key to a device, or to run a script that opens an SSH tunnel. This helps automate tasks and ensures consistency across your fleet, which is pretty handy for larger deployments.
Using AWS IoT Secure Tunneling
This is one of the best ways to get secure SSH access to your IoT devices through AWS. AWS IoT Secure Tunneling creates a protected pathway between your local machine and your distant device, all without opening up ports on the device itself to the public internet. It's a pretty neat trick.
When you start a secure tunnel, AWS IoT sets up a secure connection that goes through the AWS cloud. Your SSH traffic then travels through this tunnel, meaning it's always encrypted and only goes to the specific device you intend. This greatly reduces the chances of someone else finding and trying to get into your device.
It also helps with devices that are behind firewalls or on private networks, as you don't need to configure complex network rules. The tunnel handles the connection for you, making it simpler to manage remote access. It’s a very safe and practical approach, honestly.
To learn more about how AWS IoT Secure Tunneling works in detail, you can check out the official AWS IoT documentation. It's a great place to get the full technical rundown, so.
IAM Roles and Policies for SSH Access
AWS Identity and Access Management (IAM) is how you control who can do what in your AWS account. For SSH access, you can create specific IAM roles and policies that grant permission to open secure tunnels or manage device jobs. This means only certain people or automated processes can initiate remote connections.
For instance, you might create an IAM policy that only allows a specific user or a specific automated process to create secure tunnels to devices tagged as "production." This level of fine-grained control is really important for keeping your system secure, as a matter of fact.
Using IAM also means you don't have to share AWS account credentials directly. Instead, users assume a role with limited permissions, which is a much safer way to operate. It reduces the risk of credentials falling into the wrong hands, which is pretty significant.
Just-in-Time Provisioning for SSH Keys
Just-in-Time Provisioning (JITP) is a way to automatically register your IoT devices with AWS IoT Core when they first connect. You can extend this idea to SSH keys. Instead of pre-installing SSH keys on every device, you can use AWS IoT to push keys to devices only when they are needed.
This means that if a device is stolen or lost, it won't have an active SSH key that someone could use. The key is only valid for a short time or for a specific task. This approach makes it much harder for unauthorized access to happen, as the key is not sitting there waiting to be found.
It also helps with managing a large number of devices, as you don't have to manually put keys on each one. The system handles it for you, which saves a lot of time and effort. It's a very smart way to handle key distribution, really.
Monitoring and Logging SSH Activity
Keeping an eye on who is connecting to your devices and what they are doing is a very important part of security. AWS CloudWatch and AWS CloudTrail can help you track all activity related to your AWS IoT setup, including when secure tunnels are opened and closed.
By reviewing these logs, you can spot any unusual activity that might suggest someone is trying to get unauthorized access. For example, if you see many failed connection attempts, that could be a sign of trouble. Setting up alerts for such events is also a good idea.
Having good logs also helps you figure out what happened if something does go wrong. You can trace back the steps and understand how a problem occurred, which is crucial for learning and improving your security. It’s about having a clear record, you know.
Practical Steps for Secure IoT Device AWS IoT SSH Setup
Setting up a secure **IoT device AWS IoT SSH** connection involves a few key steps. It's not overly complicated, but each part needs to be done correctly to ensure everything works smoothly and safely. We'll go through the main things you need to do to get this working.
The basic idea is to get your device talking to AWS IoT Core, then use AWS's secure tunneling feature to create a temporary, safe path for your SSH connection. This avoids the need for direct public SSH exposure on your devices, which is a big win for security.
Remember that keeping your device software updated and following best practices for key management are also part of this process. These steps are about setting up the cloud side of things, but the device itself needs to be ready too, basically.
Setting up AWS IoT Core
First, you need to get your AWS IoT Core ready. This involves creating a "thing" in AWS IoT for each of your devices. A thing is just a record in AWS IoT that represents your physical device. This helps AWS keep track of all your connected items.
You'll also need to create a policy in AWS IoT Core. This policy defines what your device is allowed to do, like publish data or subscribe to topics. For secure tunneling, you'll need to make sure your device has the right permissions to open and manage tunnels.
Attaching the policy to your device's certificate is the next step. This links the permissions to your device's identity. It's a bit like giving your device an ID card that says what it's permitted to do in the AWS IoT system, you know.
Configuring Device Certificates
Every device that connects to AWS IoT Core needs a unique identity, and this is usually done using X.509 certificates. These certificates are like digital passports that prove your device is legitimate. They are a very important part of securing the communication.
You'll generate a certificate and a private key for each device. The certificate is registered with AWS IoT, and the private key stays on the device itself. This private key is super important and must be kept secret and safe on the device.
When your device tries to connect to AWS IoT, it uses its certificate and private key to prove its identity. This ensures that only your authorized devices can talk to your AWS IoT Core, preventing fake devices from connecting, which is pretty crucial.
Enabling Secure Tunneling
Once your devices are registered and can communicate with AWS IoT Core, you can start using secure tunneling. This involves initiating a tunnel from your local machine, specifying which device you want to connect to. AWS IoT then handles the secure connection.
On your local machine, you'll use the AWS CLI (Command Line Interface) or an SDK to create a new tunnel. You'll need to specify the device's name and the port you want to tunnel to (usually port 22 for SSH). AWS will give you a client access token for both the source and destination.
On the device side, you'll need a small piece of software that listens for tunnel connections from AWS IoT. This software, often an open-source proxy, uses the destination client access token to connect to the tunnel. Once connected, your SSH client can then use a local port to connect through the tunnel to the device's SSH server. It's a pretty elegant solution, honestly.
Device-Side SSH Configuration
Even with secure tunneling, your device still needs to have an SSH server running on it. This is usually OpenSSH, a common program found on Linux-based devices. You'll need to make sure it's installed and set up correctly.
It's also a good idea to configure your device's SSH server to only allow key-based authentication, not passwords. This is much safer, as SSH keys are very hard to guess. You'll put your public SSH key on the device, and then use your private key on your local machine to connect.
Furthermore, you should make sure the SSH server on your device is configured to only listen for connections on the local loopback interface (like 127.0.0.1). This means it won't accept direct connections from the internet, only from the secure tunnel that AWS provides. This is a very important security measure, you know.
Common Questions About IoT Device AWS IoT SSH
Can I use regular SSH directly from the internet to my IoT device?
While it's technically possible to open SSH directly to the internet on your IoT device, it's generally not a good idea for security reasons. IoT devices are often more exposed and less protected than traditional servers. Using services like AWS IoT Secure Tunneling is a much safer approach, as it avoids exposing your device's SSH port to everyone. It's about minimizing risk, you know.
What if my IoT device loses its internet connection during an SSH session?
If your IoT device loses its internet connection during an SSH session, the connection will drop. Since AWS IoT Secure Tunneling relies on the device maintaining a connection to the AWS cloud, any interruption in that connection will break the tunnel. You would need to re-establish the internet connection and then re-open the secure tunnel to regain SSH access. It's pretty straightforward in that sense.
How can I automate SSH access for a large number of IoT devices?
For a lot of devices, automating SSH access is best done using AWS IoT Jobs in combination with Secure Tunneling. You can create a job that instructs devices to open a tunnel or to prepare for a tunnel connection. You can also use AWS Lambda functions to programmatically initiate tunnels based on certain events or schedules. This helps manage things at scale, which is very useful.
Keeping Your IoT Device AWS IoT SSH Setup Safe and Sound
Once you have your **IoT device AWS IoT SSH** setup running, the work isn't quite over. Keeping it safe means ongoing attention. This includes regularly checking for updates for your device's operating system and its SSH software. New security fixes come out all the time, and staying current helps protect against new threats.
It's also a good idea to review your AWS IAM policies and IoT Core policies every now and then. Make sure that permissions are still set correctly and that no one has more access than they truly need. Limiting access to only what's necessary is a key part of good security, you know.
Monitoring your logs for unusual activity is also something you should do consistently. If you see strange connection attempts or unexpected behavior, investigate it right away. Being alert to potential problems can help you stop them before they become big issues, which is pretty important.
Conclusion
Getting into your distant IoT devices using SSH, especially with AWS IoT, is definitely possible and can be done safely. By using AWS's built-in tools like Secure Tunneling and strong identity management, you can create a reliable and protected way to manage your connected items. It's about being smart with how you set

Securing IoT Devices - AWS IoT Device Defender - AWS

Secure IoT Gateway, IoT Gateway Device - AWS IoT Core - AWS
Mastering AWS IoT Core SSH: A Comprehensive Guide To Secure IoT Device